See every device. Every connection.
Armis is the leading agentless device security platform.
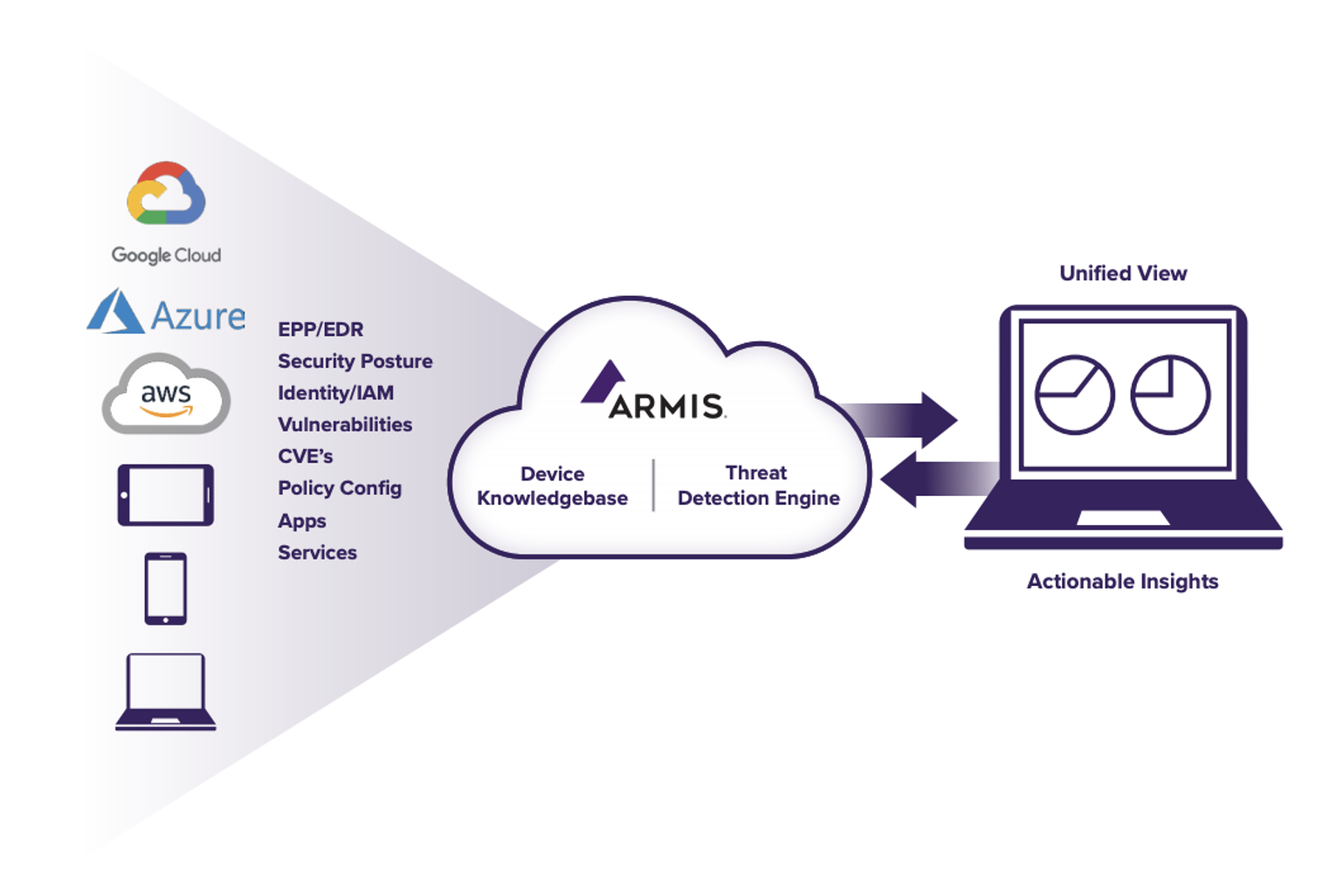
Armis is purpose-built to protect the world of unmanaged and IoT / OT devices, providing real-time and continuous cybersecurity asset management, risk management, and automated enforcement.
Comprehensive
Discovers and classifies all devices in your environment, on or off your network.
Agentless
Nothing to install on devices, no configuration, no device disruption.
Passive
No impact on your organization’s network. No device scanning.





40%
Average % of device 'unseen' by each enterprise
600M
Armis' tracked devices knowledgebase
31%
Annual growth rate of devices making way into an enterprise
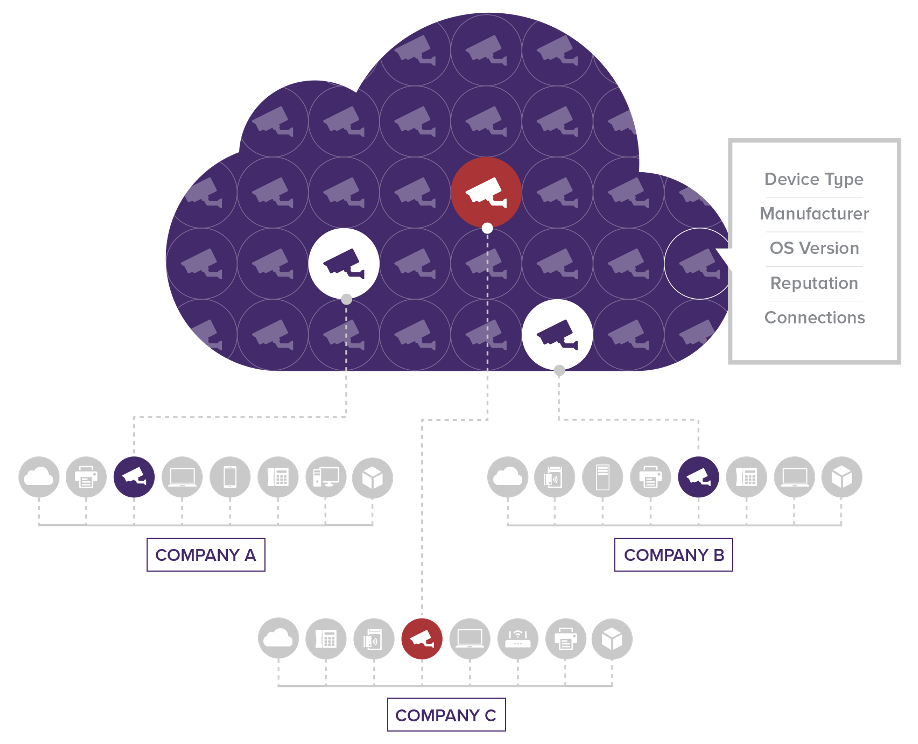
Risk Management
Armis goes beyond device and risk identification. The Armis Threat Detection Engine continuously monitors the behavior of every device on your network and in your airspace for behavioral anomalies. Working with our Device Knowledgebase, Armis compares the real-time behavior of each device.
Remote Work Security
Work From Home (WFH) created visibility and asset management challenges for these businesses as they often lack the ability to fully support a remote workforce, in a secure way
With Armis, you may discover devices used by workers remotely and at home even when not logged into the corporate network.
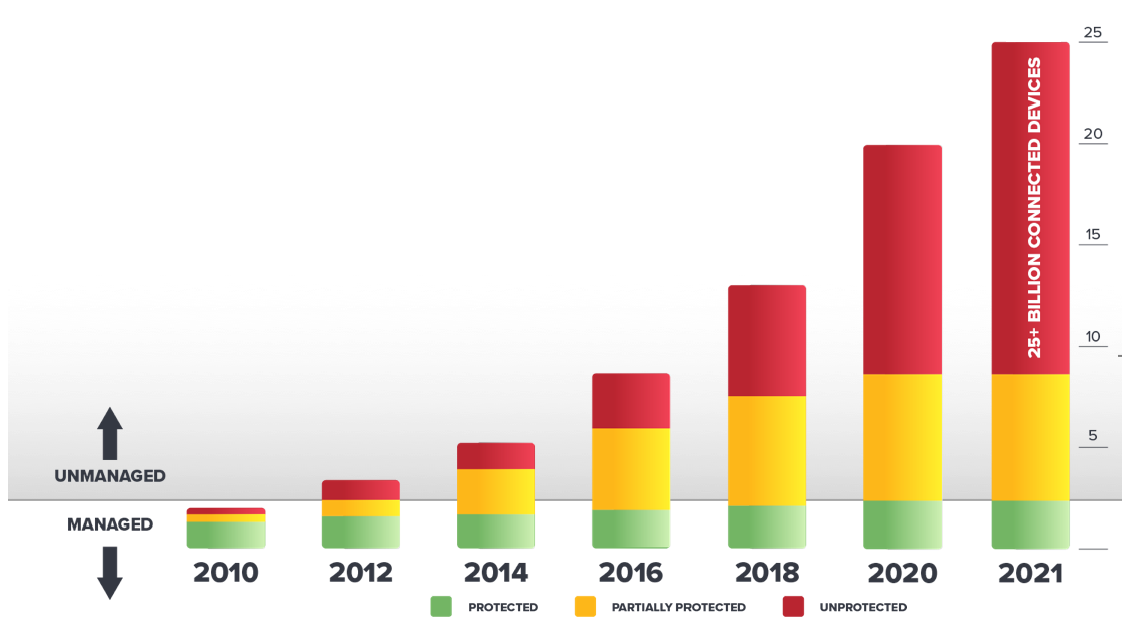
Explosion of connected devices opens a new set of cyber-threats
Growth of unmanaged devices connected to enterprise networks which can’t accommodate an agent.
Last year it was reported by Forbes that attacks against IoT devices were up 300%. See yourself why it's worth to work with Armis to protect your environment.